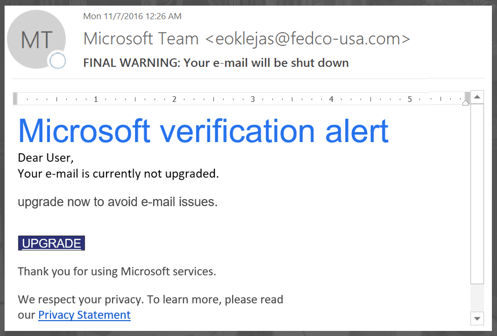
Firewalls are something we take for granted, but as we've seen from some recent high profile security breaches, even the best firewalls are imperfect. A carefully-crafted Phishing email can be tricky to spot and attackers exploit the weakest link in the security chain, which is the end user clicking on something that they shouldn't.
As part of the Intercity's Security as a Service product, offering security in the cloud or 'off-premise' network security, we thought it'd be useful to do a quick deep dive and look at how firewalls actually work in the real world.
SO, WHAT IS A FIREWALL?
We hear 'Firewall' thrown around on every spy thriller, with it posing various levels of challenges depending on your franchise of choice-- but what exactly is this invisible force? Firewalls detect and prevent attacks within network traffic, with such attacks manifesting as 'exploits', which can comprise reconnaissance as the first stage of an attack or the attack itself.
Firewalls secure all connection attempts using a technique called stateful inspection, allowing or blocking packets based not only on their header content but also the context in which they are being received.
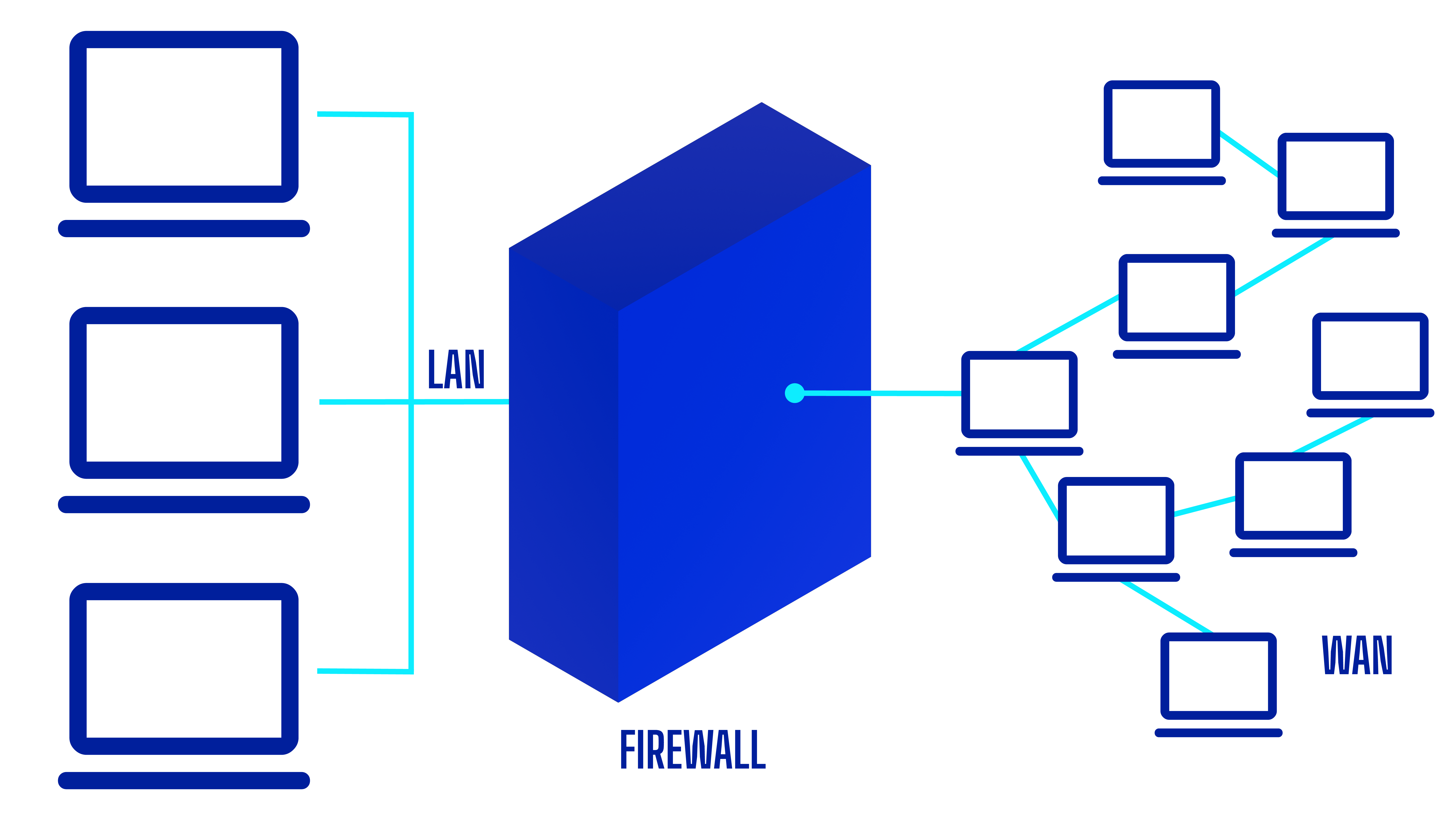
HOW DO FIREWALLS ACTUALLY WORK?
Firewalls use what are called 'screens' to detect and defend against attacks. These can be statistics-based or signature-based. Statistics-based screens detect anomalous packet arrival rate, which could be the sign of a brute-force Denial of Service (DoS) or Distributed DoS attack.
Signature-based screens inspect packet header contact, looking out for illegal settings or packet sizes which are indicative of a one-packet or two-packet kill that can cause a target to reboot, damaging its operating system.
Some of the above might sound quite sophisticated, but the main takeaway for you is that as cyber threat sophistication increases, the required skill-set for attackers is reducing.
Cybercriminals are probing continuously for vulnerabilities in operating systems - particularly Windows, as it's the most widely used - and when they find them are quick to create new exploits, not just to use themselves but to sell on to others.
Within this cybersecurity battle zone, our customers will be looking increasingly to their suppliers for thought-leadership in how to deal with cybersecurity. Discover how products such as Security as a Service can help protect your business here.
Subscribe to our newsletter
YOU MAY ALSO BE INTERESTED IN:


