Recently, whilst delving under the bonnet to find out what firewalls really do I came across the unforgettably-named Ping of Death signature-based attack or PoD.
This is what's known as a signature-based attack because it's relatively easy to recognise (so has a tell-tale signature). It's also known as a 'one/two-packet kill' because, rather than taking down a machine by a brute-force Denial of Service (DoS) attack, it achieves its objective by repeatedly sending the same malformed packet.
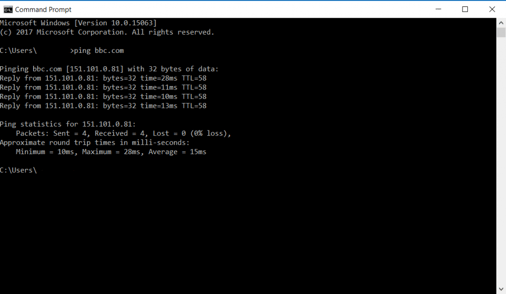
If you've not come across 'pings' before then, in brief, they provide a handy means to troubleshoot an IP connection. You can use a ping utility like this; entering the name of a host and then selecting 'start'. Provided that ping echo is enabled on the host, you'll get a response - for example, try 'bbc.com' and you'll see what happens. If any packets are lost or the round-trip time is lengthy, that's a sign of a problem.
Pings are quite simple commands, so are quite short (typically 56 bytes). PoDs exploit a vulnerability in operating systems (OS) to pings which are very long, indeed so long that they exceed the maximum permitted length of an IP packet (65,535 bytes for IPv4).
In essence, the illegal packet is fragmented by the underlying transport (e.g. Ethernet frames) for re-assembly by the recipient, which is where strange things can happen.
This re-assembly should work but in some cases, particularly with older, unpatched OSs, it doesn't. The attacker repeatedly sends PoDs which eventually overwhelm the target, causing it to crash and rendering it vulnerable to subsequent attacks, such as the injection of a Trojan or worm. Fortunately, we have a solution...
In Touch Secure, the Internet-facing firewalls contain a specific rule (or filter) which is looking out for PoDs. The key characteristics they seek are that within the packet header the protocol is ICMP (which includes the ping command) and the packet length exceeds 1,024 bytes. Whenever such a packet is received, the firewall drops it and the attack is thwarted.
This is just one of many security measures which Touch Secure provides against signature-based attacks, actively protecting our network and those of our Touch Secure customers.
[subscribe-form]
Subscribe to our newsletter
YOU MAY ALSO BE INTERESTED IN:


